Note from the Editor: This blog is part 9 of a 10-part series entitled, “Everything you need to know about an Internal Penetration Test.” To read the series from the beginning, please go to the blog, What is an Internal Penetration Test?
We often get asked how to improve the results of an internal penetration test. For a variety of reasons having a penetration test fewer critical findings is a good thing. To learn the best ways to do this, we asked our engineers for the advice. This blog shares their top 5 ways to improve the results of your penetration test.
Ways to Improve the Results of a Penetration Test
1. Patch your Systems
This is the most common theme we see across all of the penetration testing we perform. Outdated systems consistently lead to exploits and more times than not, total system compromise. Think about it for a second. When a serious vulnerability comes out and get’s reported, Microsoft (or whoever the vendor is) will resolve that vulnerability with a patch. So when you are not applying those patches, an attacker can easily exploit those vulnerabilities.
Even more risky are systems that are no longer supported. When systems are end-of-life, the vendor will no longer provide patches. Further, a lack of support means that the vendors are less likely to research or disclose vulnerabilities against the system. Over time, vulnerabilities will continue to build up on these systems. It naturally follows that the older the system, the more likely a vulnerability will be present that will allow an attacker to gain access to the system.
There are certain situations where these older systems may still be necessary, and removing them would cause a major disruption. For those systems, segment them off into their own VLAN. Restrict access to those systems as much as possible. This means as few people as possible should be able to access these systems, and as few ports as possible should be exposed. Depending on the risk, and what sensitive information this system holds, consider implementing further protections such as IDS/IPS on this segment. Finally, ensure logging and alerting is configured to alert you as soon as something happens that shouldn’t.
Ensuring your systems are patched and up to date is one of the most effective things you can do to improve the results of your penetration test.
2. Passwords, Passwords, Passwords!
One of the easiest ways for an attacker to gain access to your system is through the front door. This means accessing your administrator applications and using the default password that came with the system. This happens far too often in penetration testing, and usually gives us full control over the application or underlying host.
We have even gained access to an active directory manager using the credentials “admin:admin”. At that point, we created ourselves an account with domain administrator permissions and called the client. So how does this happen? Well, in some instances, the IT administrator was just trying to get the system working properly and forgot about it. In other instances, servers come with additional components or administrator consoles that the IT team didn’t know about.
Create Password Checklist
To fix this, we recommend creating or adopting a hardening checklist that gets used prior to a system being placed into production. This checklist should include all of the common settings to check for (SNMP community strings, default passwords, unnecessary functionality, disabling the guest account) and be followed every time. Checklists are used by pilots prior to taking off every single time. Why? Because it makes sure they don’t forget something, even if they are perfectly competent and have done it a 1,000 times. This same concept can be implemented across your IT team to ensure something doesn’t slip through the cracks. Using a hardening guide like the ones offered by NIST will quickly improve the results of your penetration test.
Perform Periodic Checks
In addition to a checklist, perform periodic checks to make sure there are no default passwords that got missed. Now that the default passwords are taken care of, it is time to remove the weak passwords on the network. This all starts with user education. If you change the password requirement to 16 characters, users will just write it down on post-it notes. If you change it to 8 characters, you will have people using ‘Company1’ as their password. What we have found is that most users have never been taught how to choose a strong password. Although user education and password policies can reduce your risk related to weak passwords, there will always be users who choose bad passwords. Because of this, wherever possible, implement multi-factor authentication to better your security posture and improve the results of your penetration test.
3. Implement Multi-Factor Authentication
One of the most successful attacks our penetration testing team uses is known as a password-spraying attack. To conduct this attack, we first do some open-source reconnaissance against your organization. One thing we are looking for is the format of your organizations usernames/email accounts. Is it First.Last@Institution.com or first initial + last name? Often it is very easy to find a few email addresses from Google, and then we can learn the pattern. Once we know that pattern, we will get a list of employees from LinkedIn. Before long, we will have a list of hundreds of usernames we can use in password attacks. In a password spraying attack, we will use a common password (Password123! for example) against a large list of usernames. By doing this, we are able to avoid account lockouts, and usually avoid setting off any alerts that would make our presence known. More times than not, within a few guesses, we have a few accounts that we can now use for an initial foothold to things like email, SharePoint, etc.
The truth is, as discussed above, you will always have users that have weak passwords. The best way to prevent this is to use multi-factor authentication. By definition multi-factor authentication requires users to authenticate using at least two of the following:
- Something you know – For example, a password.
- Something you have – For example, a smart-card or your cell phone.
- Something you are – For example a fingerprint scan.
With multi-factor authentication in place, even if an attacker guesses the password, they will still have another step they have to bypass. This exponentially reduces the likelihood you will fall victim to a password attack and ultimately improve the results of your penetration test.
4. Turn off NBNS and LLMNR
Ok this one is a bit more technical. NetBIOS Name Service (NBNS) and Link-Local Multicast Resolution (LLMNR) are methods that Windows computers use when they cannot find a host on the network. These services are vulnerable to spoofing attacks, which allow an attacker to impersonate the host you are trying to reach.
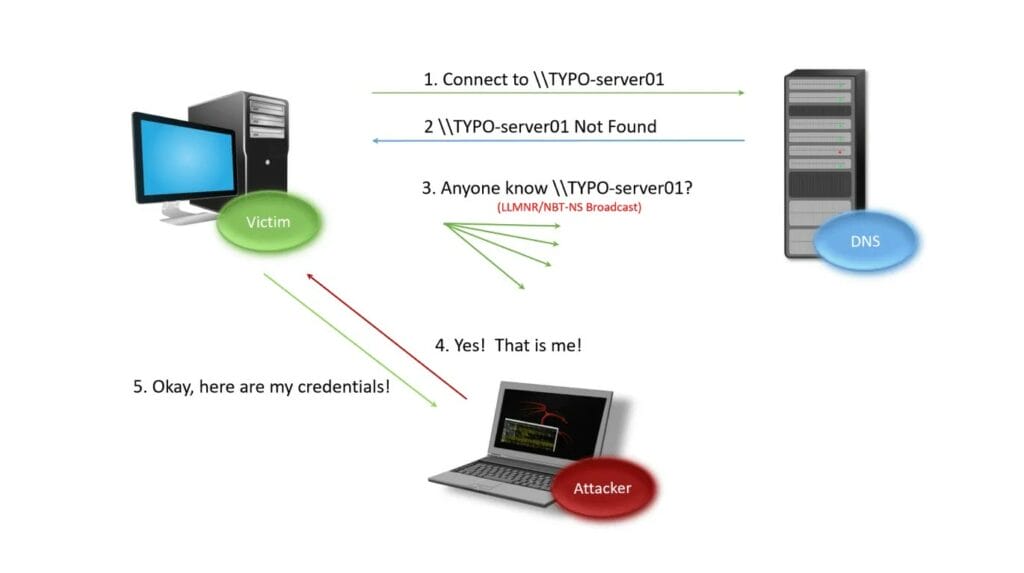
Spoofing Attack Scenario
In this scenario, lets say that you are trying to connect to a file server on the network. You mistype the name of the server (TYPO-server01). When your windows computer is trying to access this system across the network it will first check the local host file to see if it has talked to the system recently. As it is not in the local host file, your computer will then ask the DNS server where the system resides (Step 1 Above). As the system does not exist, the DNS server will be unable to assist (Step 2), so as a final resort, your Windows system will broadcast an NBNS or LLMNR request across the network (Step 3). This allows an attacker to respond to the request and receive it, claiming to be the system.
Most of the time, this is benign traffic that means nothing to the attacker. However, in the case of a file server like our example, you need to prove you have permissions to view the file or folder you are trying to access. Because of this, your computer will send your hashed (one-way encryption) password to the machine it’s trying to access. Which, in this case, is owned by the attacker. This allows the attacker to take that password offline and perform password cracking to attempt to uncover it. The above attack is the most common way we gain an initial foothold during an internal penetration test.
5. Use Unique Local Administrator Accounts
Once we gain administrator or SYSTEM level permissions to a host, it is usually a sure-thing that we will get Domain Administrator permissions on the network. At that point, it is just a matter of finding an organization’s sensitive information so we can to take some screenshots and help convey risk. Why is it a sure thing that we will get Domain Admin from a single system? Usually it is because the local administrator password on that machine is the same on most, if not all, systems on the network. Once we have SYSTEM level access on a host, we can dump contents from memory, including the SAM file which includes the password hashes for all local accounts, including Administrator. When you use that same password across the network, we can use that password hash we find to log on to all other devices, without even having to crack it.
In the past, the only way around this was an administrative nightmare. IT would have to remember (or write down/electronically store) the password for each and every machine in order for them to be unique. Luckily, Microsoft released the Local Administrator Password Solution (LAPS) to address this very issue. LAPS will automate the process of changing the password for every local administrator account across your network and keep it in a database for you.
Improve the Results of Your Penetration Test
In summary, the five steps listed above are a great way to improve the results of your penetration test. In order to keep it relatively high-level we left out a few technical details of how some of these attacks work, but hopefully it provides you with a good understanding of what the core issues are, why they are a risk to your organization, and how to resolve them. Of course, if you have any questions, please contact us. We’d love help your institution.
About the Author
Matt is Director of Penetration Testing at SIG. He currently has his PCI QSA, CISSP, OSCP, C|EH, GSEC, GCIH, and CISA certifications. You can find Matt on Twitter @InfoSecMatthew.
